What is account takeover fraud?
Account takeover fraud, or in short ATO, happens when a cybercriminal gains unauthorized access to someone’s account. Hackers usually do this for fraudulent purposes such as stealing money, making purchases, or stealing information to sell or access other accounts. Attackers commit fraud using various schemes such as phishing, malware, spyware, to name a few.
To stop account takeovers, make sure to have strong cybersecurity at hand. Two-factor authentication or multi-factor authentication, for instance, provides strong and formidable security solutions to help eliminate fraudsters and account takeovers.
How does an account takeover occur?
In an attempt to illegally take over an account, cybercriminals use several techniques. These include:
- Phishing - This fraudulent practice involves sending an email that appears to come from a reputable source to trick victims into revealing sensitive information or installing malware. Aside from email, some criminals use text messages or social media messaging services to deceive victims.
- Credential Stuffing - Using the same password on multiple (or sometimes all) accounts is a bad practice. In this cyberattack, a series of stolen login credentials from one entity is used to attempt to access other accounts or services.
- SIM Card Swapping- This scam aims to take control of a user’s digital accounts linked to a SIM. It uses the vulnerability of the two-step verification, wherein the second step is an SMS or call.
- Malware- Malware is an umbrella term for all the types of malicious software created to harm or exploit any programmable device, service, or network. This usually aims to extract data for financial gains.
- Mobile Banking Trojans- This technique steals money from a user’s mobile bank account after stealing the victim's authentication credentials by using a fake screen on top of a legitimate bank application.
- Man-in-the-Middle Attacks- This is an eavesdropping attack where the fraudster gets in the middle of an existing conversation or data transfer to acquire personal information such as login credentials, bank details, or credit card numbers.
Protection and prevention against account takeover fraud
How to detect account takeover fraud?
To detect account takeover attempts, there are some crucial signs you can look out for, as follows:
- Use of various country IP addresses- One indicator of an account takeover is a quick rise of IP addresses from one or many unusual countries. This is more likely to happen if the fraudster doesn’t know the legitimate account owner’s original location.
- Changing different accounts with shared details- If you notice different accounts making comparable or similar changes to a shared detail, you may be under an account takeover attack.
- Unknown devices- As preparators usually hide the device they use, detecting unknown devices attempting to access multiple accounts is a clear sign of an account takeover in action.
- Multiple accounts accessed by the same device - Some fraudsters may not try to hide or spoof their devices. If you’re spotting more than one of your accounts linked to one device, it may be a manifestation of an account takeover.
How to Prevent Account Takeover Fraud?
Here's a list of cybersecurity you can use to prevent account takeover fraud:
- Tracking system - Sandboxing, or a method of creating an isolated test environment, can help monitor all activities related to an account.
- Web application firewall - Web Application Firewall (WAF) can help identify and block account takeover attacks through targeted policies.
- AI-based detection - With AI-based security, even sophisticated account takeover attempts can be easily resolved while effectively monitoring a website for any unusual activities.
- Multi-Factor Authentication - Deploying multi-factor authentication is the key to preventing or stopping account takeovers. Attackers will never access an account without the authentication sent only to the legitimate users.
Modern and secure authentication solution against account takeovers
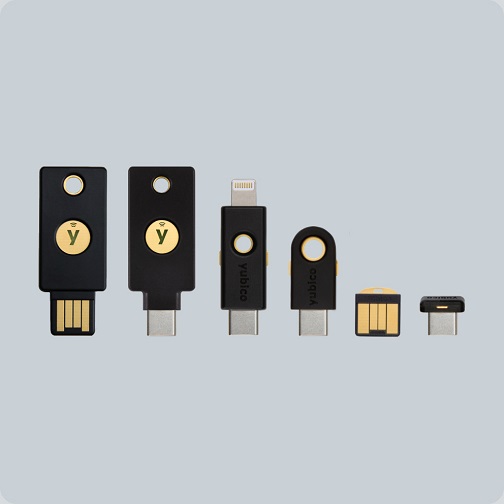
Designed for optimum security, Yubikey holds the authentication standards for the modern web.
-
What is Yubikey?
Yubikey is the leading security key and the only authentication technology proven to stop account takeovers at scale. It works with hundreds of services with an all-in-one configurable security key for high-quality protection. -
How will Yubikey stop account takeovers? Yubikey enables strong two-factor, multi-factor, and passwordless authentication that prevents hackers and account takeovers from having successful attempts and attacks.
With the highest level of security and privacy, Yubikey solutions are your one key to multiple security needs. Yubico security keys include powerful security tools such as Yubico U2F Security Key, YubiKey 5 NFC, YubiKey 5Ci, Yubico Security Key NFC, YubiKey 5C NFC, YubiKey 5 Nano, and YubiKey Bio.
Want to avail Yubico products? Contact +63 2 8858 5555 today!